The Scope of Cyber-risk: Why Cybercriminals Exploit U.S. Government Elections
August 17, 2021
There is consensus among government entities and stakeholders from the cybersecurity industry and the private sector: we need to detect, disrupt, and respond to interference with election apparatus more effectively.
Government elections are an attractive target for cybercriminals aiming to disrupt and destabilize the foundations of U.S. democracy.
Elections comprise a heterogenous and fluid ecosystem and involve many moving parts and players: the voting public, high-risk/high-profile election candidates, campaign teams, departments and agencies, contractors, election staff and volunteers, businesses, the media, and more.
Cybercriminals seek to exploit any potential weak links introduced by this complexity.
Official election workers, who have access to systems and databases, are popular targets. Threat actors will look for ways to capitalize on this privileged status to exfiltrate sensitive material and information or even lock down campaign operations through coordinated malware and ransomware attacks.
Although poll worker volunteers are unlikely to have access to core election infrastructure, they typically log onto the networks at polling locations via their laptops or other mobile devices. By successfully targeting a volunteer’s personal device, attackers could find a back door in the network, grant themselves privileges, and move laterally throughout the network to launch a ransomware or other attack on polling precincts.
To illustrate the magnitude and scope of the cyber-risk presented by government elections, consider this visual based on information from the National Institute of Standards and Technology (NIST).
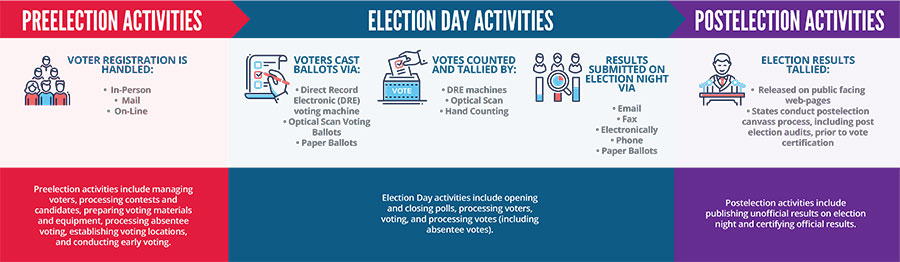
How Can We Keep Votes Safe and Secure?
Securing the future of U.S. elections calls for a particularly sharp focus on identity and access management.
Download White Paper ›